
 Enhance Your Cybersecurity with
Enhance Your Cybersecurity with
MG Datacomm’s Security Solutions
Empowering Australian businesses to stay resilient against evolving cyber threats.
Our cybersecurity solutions help Australian businesses achieve robust cybersecurity through proactive monitoring, threat detection,
and tailored security measures.
Ensure your business meets the ACSC Essential Eight Maturity Level 2 as a standard.
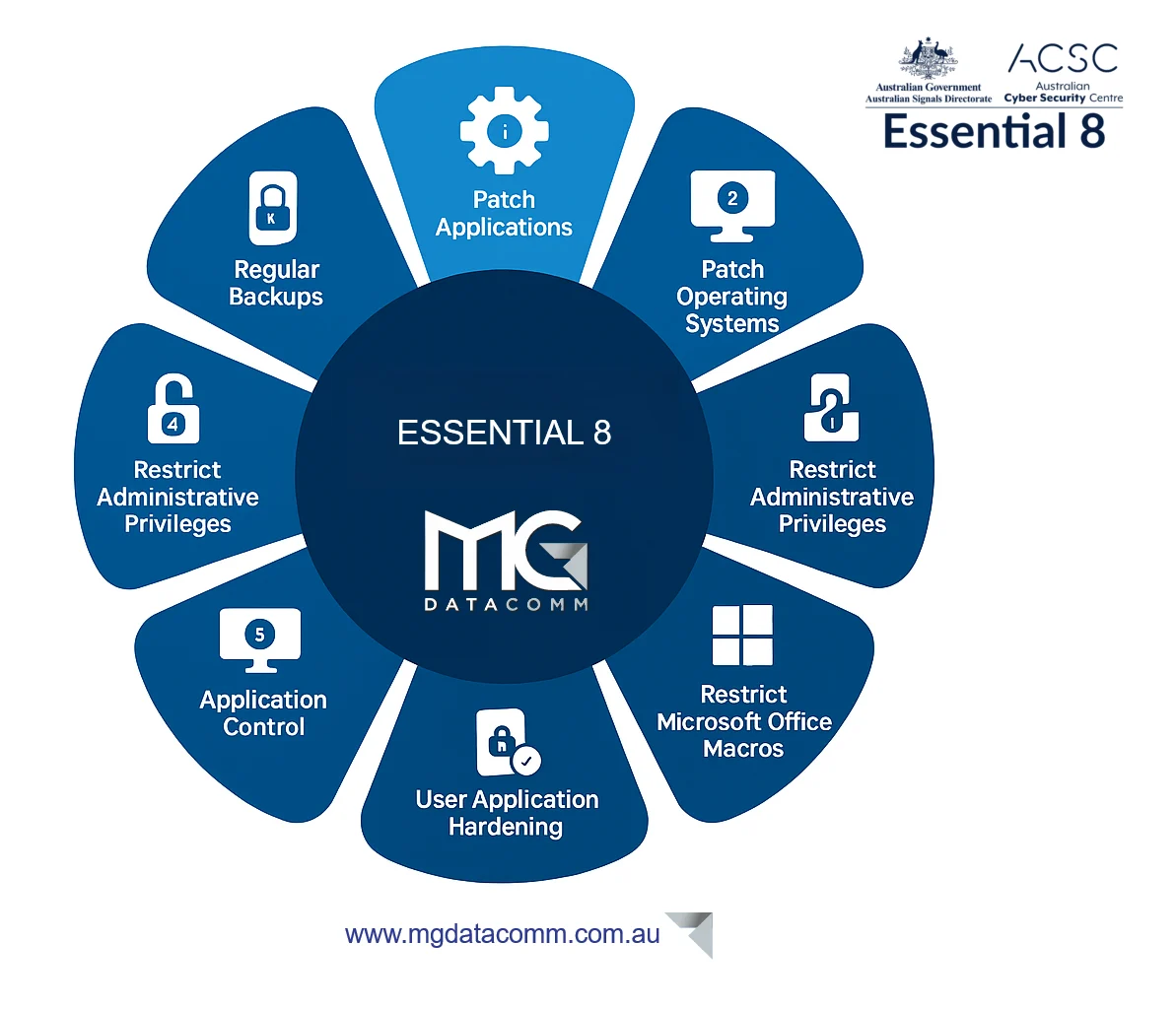
 Compliance with the ACSC Essential Eight
Compliance with the ACSC Essential Eight
Strengthen your cybersecurity posture with MG Datacomm by aligning with the ACSC Essential Eight. Our tailored Security Services help you achieve and maintain compliance, providing a structured approach to mitigate cyber risks.
Leverage our expertise to identify gaps, implement best practices, and continuously monitor your security landscape. At MG Datacomm, we ensure your business stays resilient against evolving threats, safeguarding your success.
Ready to strengthen your cybersecurity posture with a trusted partner?
Find out how MG Datacomm can help your company manage risk,
respond to incidents and bolster your cyber resilience.
We’ll help you identify gaps, strengthen your defenses, and stay compliant. Whether you need a
one-off audit or fully managed protection—we’re here to help.

Security Baseline Assessment
Ideal for:
Businesses that need to understand their security posture and identify vulnerabilities
before making improvements.
Includes:![]() Cybersecurity Maturity Assessment (aligned with ACSC Essential 8)
Cybersecurity Maturity Assessment (aligned with ACSC Essential 8)![]() Vulnerability & Risk Analysis (on-premises & cloud environments)
Vulnerability & Risk Analysis (on-premises & cloud environments)![]() Privilege & Access Review (identifying excessive admin rights & shadow IT)
Privilege & Access Review (identifying excessive admin rights & shadow IT)![]() Security Findings Report with risk ratings & tailored recommendations
Security Findings Report with risk ratings & tailored recommendations![]() Roadmap for Security Uplift to improve maturity over
Roadmap for Security Uplift to improve maturity over
Choose this for:
• Establish a clear security baseline
• Identify critical risks & compliance gaps
• Provide tailored recommendations for a security roadmap
• Enables a structured path for improvement, without ongoing commitment

Security Uplift & Hardening
Ideal for:
Businesses needing to improve their security posture based on an assessment or
known security gaps.
Includes:![]() Implementation of Essential 8 Controls
Implementation of Essential 8 Controls![]() Hardening of M365, Azure AD, Endpoints & Network Security
Hardening of M365, Azure AD, Endpoints & Network Security![]() Privileged Access & Identity Management Enhancements
Privileged Access & Identity Management Enhancements![]() Security Awareness Training for Employees
Security Awareness Training for Employees![]() Firewall & Endpoint Security Policy Configuration
Firewall & Endpoint Security Policy Configuration
Choose this for:
• Delivers measurable improvements in security maturity
• Proactively closes security gaps to reduce risk exposure
• Aligns with industry compliance requirements (ISO 27001, Essential 8, NIST 2.0, etc.)
• Flexible uplift projects based on business risk & priorities

Fully Managed Cybersecurity
Ideal for:
Businesses needing continuous protection, monitoring, and compliance management
Includes:![]() All Security Uplift & Hardening, plus:
All Security Uplift & Hardening, plus:![]() 24/7 Security Monitoring (SOC-as-a-Service)
24/7 Security Monitoring (SOC-as-a-Service)![]() Managed SIEM (Security Information & Event Management)
Managed SIEM (Security Information & Event Management)![]() Monthly Security Reviews & Threat Intelligence Reports
Monthly Security Reviews & Threat Intelligence Reports![]() Proactive Threat Hunting & Incident Response Readiness
Proactive Threat Hunting & Incident Response Readiness![]() Regular Vulnerability Scanning & Patch Management
Regular Vulnerability Scanning & Patch Management
Choose this for:
• Provides real-time security monitoring & rapid incident response
• Ensures ongoing compliance & security hygiene
• Protects against advanced threats & evolving attack vectors
• Monthly reporting to track security improvements over time
